Hi,
I would like to know if at the end with all changes in IOS security last years, if it is possible that the app for cordova in iOS keeps cookies from server and send to the server on every request.
I tried a lot of configurations in the preferences config.xml file, the CORS’s related configuration on the server, etc, also checked this topic Cordova cookies not working iOS 14 (ITP) that looks like there is not solution but it is from 2022. So, it is possible to keep cookies for handle the session in the iOS app at this days? or really it is not possible, so I will not spend more time on this?
Thank you.
I believe certain types of cookies will work, but ITP blocks 3rd party cookies by default. If you can explain what you’re trying to do we might be able to help further.
Hi,
My app has a login form and that makes an ajax call to a webservice. That webservice responds with a session id by a secure cookie, but looks like the cookie is not read by the app, so next calls, doesn’t contains the cookie and the session is lost. In Android works fine. My calls are only to one domain.
This sounds like the very definition of a 3rd party cookie. One option might be to use a non-browser based request plugin, like cordova-plugin-advanced-http - npm
There are several plugins that allow you to bypass the browser’s built in fetch restrictions. However, if you have control of the API, I would suggest not returning the login token in a cookie. That will make this much easier.
Thank for the quick answer.
One option might be to use a non-browser based request plugin, like cordova-plugin-advanced-http - npm
The app loads all the html code into and is used not only by android and iOS, it is used by a regular browser too.
There are several plugins that allow you to bypass the browser’s built in
fetchrestrictions. However, if you have control of the API, I would suggest not returning the login token in a cookie. That will make this much easier.
I have control on the app and server API, but I can’t change that logic, because Android and regular browsers are using it as it should and I feel that a secure cookie in the cordova app is more secure than a token in memory or localstorage.
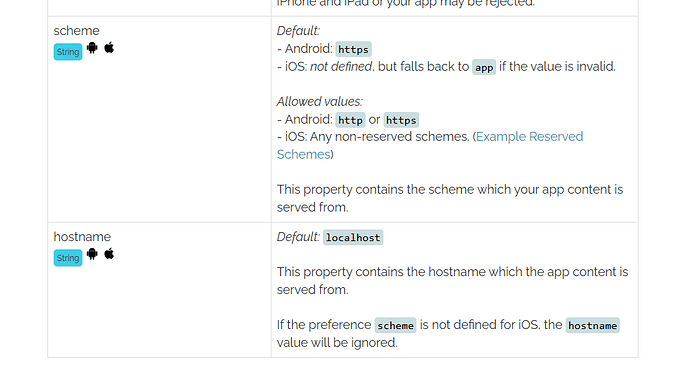
I wonder why the app “thinks” it is a 3rd party cookie. I tried to set the doman in the config.xml, but if I query to the document.location.href, it shows app:// if I set the schema in preferences or file:// if not, so probably that’s is why an ajax query to mydomain.com is like a 3rd party.
This doesn’t preclude you from creating a wrapper using non-browser methods to make the auth call.
I’m not sure what you’re basing this on, but I would like to understand. To my understanding, cookie storage, local storage and all the various site based storage solutions all use the same underlying store and have the same security.
For iOS, you can’t use a reserved schema, as references in the docs here: Config.xml API - Apache Cordova - that means that you can’t set your schema to https, which would be required as a third party cookie pays attention to both the schema and hostname.
I’m not sure what you’re basing this on, but I would like to understand. To my understanding, cookie storage, local storage and all the various site based storage solutions all use the same underlying store and have the same security.
You can access from jscript to the localstorage, but you cannot acces with jscript to a secure cookie.
For iOS, you can’t use a reserved schema, as references in the docs here: Config.xml API - Apache Cordova - that means that you can’t set your schema to https, which would be required as a third party cookie pays attention to both the schema and hostname.
If understood, means that every xhr call will be managed as different from the base domain, so all cookies will be as 3rd party, so there is no way for cordova for iOS to handle that “regular” web behavior.
I’m fairly certain even secure first party cookies are available in document.cookie - I haven’t seen anything to the contrary. You may be referencing the HttpOnly property, which does omit the cookies from document.cookie, but 3rd party cookies will soon stop working in any browser and so attempting to access an API from a different domain will need some other method of authenticating that doesn’t involve a 3rd party cookie. Even OAuth2 returns the token as a JSON request body.
As I said, 3rd party cookies have stopped working or will stop working in all browsers soon. This is in no way regular web behavior. In Cordova the proper way to deal with this is to use a plugin to make the request - or to use an API that doesn’t depend on HttpOnly cookies to operate.
Your are right, I was referencing to HttpOnly, not to the secure. I understand that 3rd party cookies option will expire, but why the webkit thinks it is a call to a different domain? how I can set the base or multiple domains so the calls are not treated as 3rd party cookies?
I’m reading some docs about webkit for iOS (I think webkit is used by Cordova). App-Bound Domains | WebKit . Not sure if when compile the app in VOLT, there is some place to config the possible domains.
how I can set the base or multiple domains so the calls are not treated as 3rd party cookies?
You can’t. While you can set the domain using the hostname preference, you can’t set the schema to https on iOS since it’s reserved. Since the schema doesn’t match, I believe the browser will look at the entire URI and decide the cookie is 3rd party. Your API is simply not compatible with calls from 3rd party domains. The best solution in this case is to use a fetch style plugin that bypasses browser restrictions when you’re in the Cordova environment. Otherwise, use the browser’s fetch implementation. The only other option is to change your API.
App-bound domains seem to be designed to restrict the browser further, rather than loosening restrictions so I doubt that will help, but you can always use config-file or edit-config to modify the Info.plist.
If you find another solution please let us know about it.